94. Ubiquiti UniFi
Ubiquiti UniFi is an enterprise solution for managing wireless networks. The UniFi infrastructure is managed by the UniFi Controller, which can be configured to send logs to a remote Syslog server via UDP. As a central management point, it will make sure that logs from all access points, including client authentication messages, are logged to the Syslog server.
More information about configuring the UniFi Controller can be found in the corresponding user guide.
|
Note
|
The steps below have been tested with UniFi Controller v4 and should work for other versions also. |
-
Configure NXLog for receiving Syslog log entries via UDP (see the examples below). Then restart NXLog.
-
Make sure the NXLog agent is accessible from the server with the Controller software.
-
Log in to the Controller’s web interface.
-
Go to .
-
Select Enable remote syslog server and specify the IP address and UDP port that the NXLog agent is listening on. If necessary, also select Enable debug level syslog. Then click Apply.
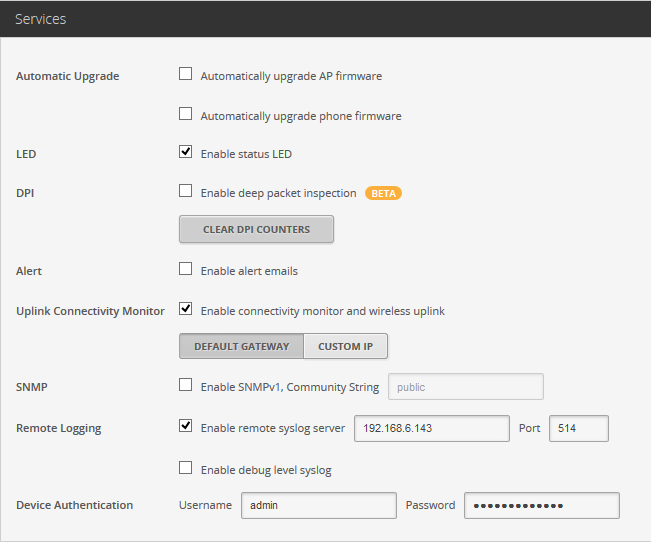
By default, the UniFi Controller sends a lot of low level information
which may complicate field extraction if additional intelligence is
required. The Syslog level can be adjusted individually for each access
point from the Controller server by changing the syslog.level value in
the system.cfg file. The location of this file varies depending on the
host operating system. If the Controller software is running on Windows,
the file can be found under C:\Ubiquiti
UniFi\data\devices\uap\<AP_MAC_ADDRESS>
Unfortunately, once configured with remote Syslog address, the
Controller only sends log messages that originate from access
points. The Controller’s own log is located on the server where it is
installed. The location of this file depends on the host operating
system, on Windows it can be found at C:\Ubiquiti
UniFi\logs\server.log. If needed, this file can be parsed with the
om_file module.
This example shows UniFi logs as received and processed by NXLog.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
<Extension _syslog>
Module xm_syslog
</Extension>
<Extension _json>
Module xm_json
</Extension>
<Input in_syslog_udp>
Module im_udp
Host 0.0.0.0
Port 514
Exec parse_syslog();
</Input>
<Output file>
Module om_file
File "/var/log/unifi.log"
Exec to_json();
</Output>
{
"MessageSourceAddress": "192.168.10.147",
"EventReceivedTime": "2017-04-27 19:38:55",
"SourceModuleName": "in_syslog_udp",
"SourceModuleType": "im_udp",
"SyslogFacilityValue": 3,
"SyslogFacility": "DAEMON",
"SyslogSeverityValue": 6,
"SyslogSeverity": "INFO",
"SeverityValue": 2,
"Severity": "INFO",
"Hostname": "192.168.10.147",
"EventTime": "2017-04-27 19:40:44",
"Message": "(\"U7P,0418d6809ce2,v3.7.11.5131\") hostapd: ath4: STA 34:02:86:45:8e:e0 IEEE 802.11: disassociated"
}Additional fields can be extracted from the Syslog messages with a configuration like the one below.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
<Input in_syslog_udp>
Module im_udp
Host 0.0.0.0
Port 514
<Exec>
parse_syslog();
if $Message =~ / ([a-z]*): (.*)$/
{
$UFProcess = $1;
$UFMessage = $2;
if $UFMessage =~ /^([a-z0-9]*): (.*)$/
{
$UFSubsys = $1;
$UFMessage = $2;
if $UFMessage =~ /^STA (.*) ([A-Z0-9. ]*): (.*)$/
{
$UFMac = $1;
$UFProto = $2;
$UFMessage = $3;
}
}
}
</Exec>
</Input>
{
"MessageSourceAddress": "192.168.10.149",
"EventReceivedTime": "2017-05-01 20:30:13",
"SourceModuleName": "in_syslog_udp",
"SourceModuleType": "im_udp",
"SyslogFacilityValue": 3,
"SyslogFacility": "DAEMON",
"SyslogSeverityValue": 6,
"SyslogSeverity": "INFO",
"SeverityValue": 2,
"Severity": "INFO",
"Hostname": "192.168.10.149",
"EventTime": "2017-05-01 20:32:11",
"Message": "(\"U7P,0418d6809b78,v3.7.11.5131\") hostapd: ath2: STA 80:19:34:97:62:a6 RADIUS: stopped accounting session 5907CFDD-00000002",
"UFProcess": "hostapd",
"UFSubsys": "ath2",
"UFMac": "80:19:34:97:62:a6",
"UFProto": "RADIUS",
"UFMessage": "stopped accounting session 5907CFDD-00000002"
}