68. McAfee Enterprise Security Manager (ESM)
McAfee Enterprise Security Manager (ESM) is a security information and event management (SIEM) solution that can collect logs from various sources and correlate events for investigation and incident response. For more information, see McAfee Enterprise Security Manager on McAfee.com.
NXLog can be configured to collect events and forward them to ESM. This chapter provides information about setting up NXLog to forward events from several types of log sources.
|
Note
|
The instructions and examples in this chapter were tested with ESM 11.2.0. |
68.1. Configuring McAfee ESM
The following steps may be required to prepare ESM for receiving events from NXLog.
68.1.1. Set up TLS Transport
NXLog can send logs to ESM securely with TLS. This can be set up as follows. For more information about generating certificate and key files, see OpenSSL Certificate Creation.
-
Create or locate a certificate authority (CA) certificate and private key. The CA certificate (for example,
rootCA.pem) will be used by the NXLog agent to authenticate the ESM receiver in Forwarding Logs below. -
Create a certificate and private key for ESM (for example,
server.crtandserver.key). -
Upload the
server.crtandserver.keyfiles to ESM (for more information, see Install SSL certificate on McAfee.com):-
On the McAfee web interface, open the menu in the upper left corner, click on System Properties, and choose ESM Management in the left panel.
-
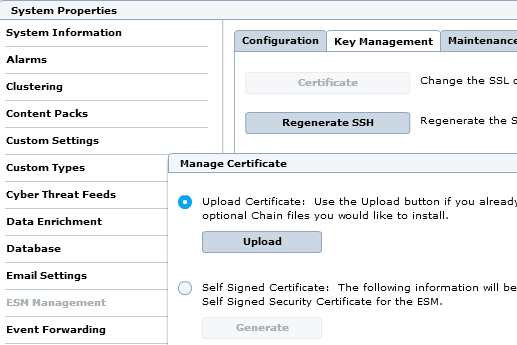
Open the Key Management tab and click Certificate.
-
Select Upload Certificate, click Upload, acknowledge the notification, and upload the certificate files.
-
-
When adding or editing a log source, check Require syslog TLS (see Adding a Log Source below).
68.1.2. Adding a Log Source
Each log source type must have a corresponding data source (or parent source) configured in the ESM local receiver.
-
On the McAfee web interface, open the menu in the upper left corner and click on More Settings.
-
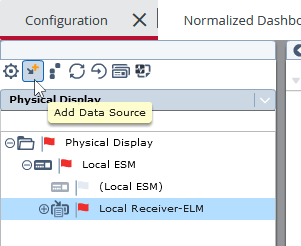
Select the Local Receiver-ELM in the left panel and click on Add Data Source.
-
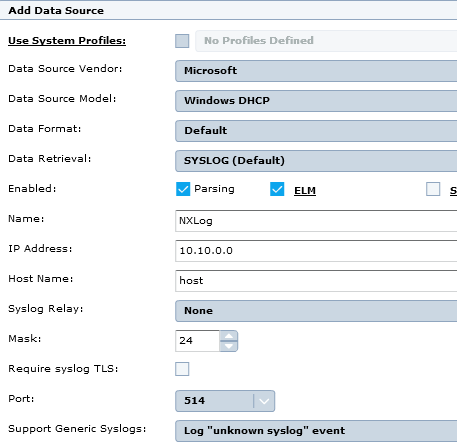
Choose a Data Source Vendor, Data Source Model, Data Format, and Data Retrieval. Consult the sections below for the correct values to use for each log source type.
-
Enable Parsing, and ELM storage if required.
-
Enter appropriate Name, IP Address, and Host Name values.
-
For Syslog Relay, select None.
-
Enter a Mask to use an IP address range, if required.
-
To require TLS transport, check Require syslog TLS (see Set up TLS Transport).
-
For Port, use the default of 514 or click Interface to change the available Syslog ports.
-
For Support Generic Syslogs, select Log "unknown syslog" event.
-
Click OK to save the changes. When the Apply Data Source Settings dialog appears, click Yes. Then click OK on the Rollout window to deploy the changes.
68.2. Sending Specific Log Types for ESM to Parse
To take full advantage of ESM’s log parsing and rules, NXLog can be configured to send log types in a format expected by ESM. A few common log types are shown here.
68.2.1. DHCP Server
In order to send DHCP Server audit log events to ESM, set up DHCP Audit Logging and use the NXLog configuration below. When adding an ESM data source, use the following parsing configuration (see Adding a Log Source):
| Field | Value |
|---|---|
Data Source Vendor |
Microsoft |
Data Source Model |
Windows DHCP |
Data Format |
Default |
Data Retrieval |
SYSLOG (Default) |
For more information, see DHCP Server Audit Logging and the Microsoft DHCP Server page in the McAfee ESM Data Source Configuration Reference Guide.
In this example, NXLog is configured to read logs from the
DhcpSrvLog and DhcpV6SrvLog log files.
NXLog then adds a Syslog header with xm_syslog to
prepare the events for forwarding to ESM.
64,08/31/19,14:38:17,No static IP address bound to DHCP server,,,,,0,6,,,,,,,,,0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
<Extension _syslog>
Module xm_syslog
</Extension>
<Input dhcp>
Module im_file
File 'C:\Windows\System32\dhcp\DhcpSrvLog-*.log'
File 'C:\Windows\System32\dhcp\DhcpV6SrvLog-*.log'
<Exec>
# Discard header lines
if $raw_event !~ /^\d+,/ drop();
# Add Syslog header
$Message = $raw_event;
to_syslog_bsd();
</Exec>
</Input>
<13>Aug 31 14:38:17 Host 64,08/31/19,14:38:17,No static IP address bound to DHCP server,,,,,0,6,,,,,,,,,068.2.2. DNS Debug Log
In order to send DNS debug log events to ESM, enable debug logging and use the NXLog configuration below. When adding an ESM data source, use the following parsing configuration (see Adding a Log Source):
| Field | Value |
|---|---|
Data Source Vendor |
Microsoft |
Data Source Model |
Windows DNS |
Data Format |
Default |
Data Retrieval |
SYSLOG (Default) |
For more information, see Windows DNS Server and the Microsoft DNS Debug page in the McAfee ESM Data Source Configuration Reference Guide.
The following configuration uses im_file to read from the Windows DNS debug log. A Syslog header is added with the xm_syslog to_syslog_bsd() procedure.
8/31/2019 15:17:04 PM 2AE8 PACKET 00000005D03B4CE0 UDP Snd 192.168.1.42 fdd7 R Q [8081 DR NOERROR] A (9)imap-mail(7)outlook(3)com(0)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
<Extension _syslog>
Module xm_syslog
</Extension>
<Input in>
Module im_file
File 'C:\logs\dns.log'
<Exec>
# Discard header lines
if $raw_event !~ /^\d+\/\d+\/\d+/ drop();
# Add Syslog header
$Message = $raw_event;
to_syslog_bsd();
</Exec>
</Input>
<13>Aug 31 15:17:04 Host 8/31/2019 15:17:04 PM 2AE8 PACKET 00000005D03B4CE0 UDP Snd 192.168.1.42 fdd7 R Q [8081 DR NOERROR] A (9)imap-mail(7)outlook(3)com(0)68.2.3. Windows Event Log
Microsoft Windows Event Log data can be collected and sent to McAfee ESM with the NXLog configuration below. When adding an ESM data source, use the following parsing configuration (see Adding a Log Source):
| Field | Value |
|---|---|
Data Source Vendor |
Microsoft |
Data Source Model |
Windows Event Log – CEF |
Data Format |
Default |
Data Retrieval |
SYSLOG (Default) |
For more information about collecting Windows Event Log, see the Windows Event Log chapter.
In this configuration, Windows Event Log data is collected from the Security channel with im_msvistalog and converted to CEF with a Syslog header.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
<Extension _cef>
Module xm_cef
</Extension>
<Extension _syslog>
Module xm_syslog
</Extension>
<Input eventlog>
Module im_msvistalog
Channel Security
<Exec>
$Message = to_cef();
to_syslog_bsd();
</Exec>
</Input>
<14>Sep 25 23:25:53 WINSERV Microsoft-Windows-Security-Auditing[568]: CEF:0|NXLog|NXLog|4.99.5128|0|-|7|end=1569453953000 dvchost=WINSERV Keywords=9232379236109516800 outcome=AUDIT_SUCCESS SeverityValue=2 Severity=INFO externalId=4801 SourceName=Microsoft-Windows-Security-Auditing ProviderGuid={54849625-5478-4994-A5BA-3E3B0328C30D} Version=0 TaskValue=12551 OpcodeValue=0 RecordNumber=395661 ActivityID={61774D29-73EB-0000-4B4D-7761EB73D501} ExecutionProcessID=568 ExecutionThreadID=3164 deviceFacility=Security msg=The workstation was unlocked.\r\n\r\nSubject:\r\n\tSecurity ID:\t\tS-1-5-21-2262720663-2632382095-2856924348-500\r\n\tAccount Name:\t\tAdministrator\r\n\tAccount Domain:\t\tWINSERV\r\n\tLogon ID:\t\t0x112FE1\r\n\tSession ID:\t1 cat=Other Logon/Logoff Events Opcode=Info duid=S-1-5-21-2262720663-2632382095-2856924348-500 duser=Administrator dntdom=WINSERV TargetLogonId=0x112fe1 SessionId=1 EventReceivedTime=1569453953949 SourceModuleName=eventlog SourceModuleType=im_msvistalog68.3. Forwarding Logs
Use an output instance to forward the processed logs to McAfee ESM. The
configurations shown below can be used with any of the above input
instances. Because all event formatting is done in the input sections, the
output instances here do not require any Exec directives
(the $raw_event field is passed without any further modification).
This om_tcp instance sends logs to ESM via TCP. In this example, events are sent from the Windows Event Log source.
Forwarding logs with TLS requires adding a certificate to ESM and setting Require syslog TLS on the data source(s), as described in the Set up TLS Transport section.
The om_ssl module is used here to send logs to ESM securely, with TLS encryption.